

WPSPin-v1.0.5.apk
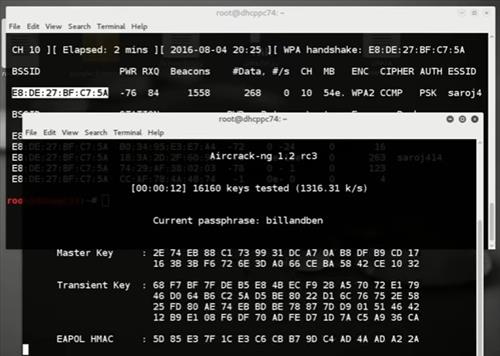
Put the printer in WPS connection mode. Printers with a touchscreen control panel: Open the Setup, Network, or Wireless settings menu, select Wi-Fi Protected Setup, select Push Button, and then select Start. Printers without a touchscreen control panel: Press and hold the Wireless button for five seconds until the wireless light flashes. This exploit defeats WPS via an intelligent brute-force attack to the static WPS PIN. It can be misused to brute-force the WPS PIN and enable recovery of the WPA passphrase in an incredibly short. Offline WPS PIN Companion from Router Scan. Uses known algorithms, does not use database. Online 3WiFi WPS PIN generator. Takes advantage of collected data in the database, detects linear sequences, static PIN codes, and other algorithms. Select the document file in the TXT format to convert to the WPS format, you can select a file from your computer or your Google Drive or Dropbox account. STEP 2 Choose the WPS format from the drop-down list as the output format, and click the Convert button, you can convert up to 5 files at the same time and a maximum size of up to 300 MB. This is a complete collection of default WPS pin's for user's to check before spending hour's Brute forcing. (peace) TP-LINK Devices WPS-PIN: 66870913 Essid: TP-LINK777; TP-LINKFD69D0 after reset Router model: TL-WR741N Router model: TL-WR841N WPS-PIN: 85075542 Router model: TL-WR842ND WPS-PIN: 55117319 MODEL: TD-W8960N BSSID: 74:EA:3A:BC:75:D6 WPS: 37211202.
A router with WPS requires a PIN to allow other devices to connect, and this PIN should be unique to every router and not derived from other easily accessible data found on the router. When [Craig] took a look at the firmware of a D-Link DIR-810L 802.11ac router, he found exactly the opposite; the WPS PIN was easily decipherable because it was generated entirely from the router’s MAC address and could be reverse engineered by sniffing WiFi.
When [Craig] was taking a look at the disassembled firmware from his router, he noticed a bit of code that accessed the NVRAM used for storing device-specific information like a serial number. This bit of code wasn’t retrieving a WPS pin, but the WAN MAC address instead. Instead of being unique to each device and opaque to every other bit of data on the router, the WPS pin was simply generated (with a bit of math) from the MAC address. This means anyone upstream of the router can easily derive the WPS pin of the router, and essentially gives everyone the keys to the castle of this router.

Wps Pin List Txt File
A few years ago, it was discovered the WPS pin was extremely insecure anyway, able to be brute-forced in a matter of minutes. There are patches router manufacturers could apply to detect these brute force attacks, closing that vulnerability. [Craig]’s code, though, demonstrates that a very large number of D-Link routers effectively broadcast their WPS PIN to the world. To make things even worse, the BSSID found in every wireless frame is also derived from the WAN MAC address. [Craig] has literally broken WPS on a huge number of D-Link routers, thanks to a single engineer that decided to generate the WPS PIN from the MAC address.
WPSPin-v1.0.4.apk
[Craig] has an incomplete list of routers that are confirmed affected on his site, along with a list of confirmed unaffected routers.