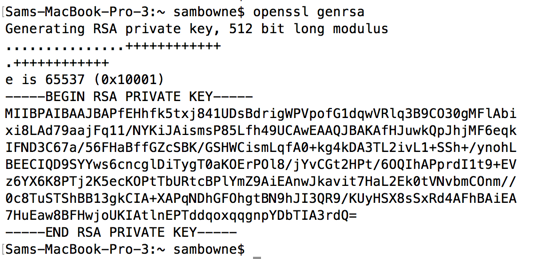
Generating an RSA Private Key Using OpenSSL. You can generate an RSA private key using the following command: openssl genrsa -out private-key.pem 3072. In this example, I have used a key length of 3072 bits. While 2048 is the minimum key length supported by specifications such as JOSE, it is recommended that you use 3072. You want to use RSA to encrypt data, and you need to generate a public key and its corresponding private key. Use a cryptography library's built-in functionality to generate an RSA key pair. Here we'll describe the OpenSSL API. If you insist on implementing RSA yourself (generally a bad idea), see the following discussion.
- Openssl Generate Rsa Key Pair And Certificate
- Openssl Generate Rsa Key Pair C++
- Openssl Rsa Generate Key Pair Chart
This topic describes using key pair authentication and key pair rotation in Snowflake.
In this Topic:
Overview¶
Snowflake supports using key pair authentication for enhanced authentication security as an alternative to basic authentication (i.e.username and password).
This authentication method requires, as a minimum, a 2048-bit RSA key pair. You can generate the Privacy Enhanced Mail (i.e. PEM)private-public key pair using OpenSSL. Some of the Supported Snowflake Clients allow using encrypted private keys to connect toSnowflake. The public key is assigned to the Snowflake user who uses the Snowflake client to connect and authenticate to Snowflake.
Snowflake also supports rotating public keys in an effort to allow compliance with more robust security and governance postures.
Supported Snowflake Clients¶
The following table summarizes support for key pair authentication among Snowflake Clients. A checkmark (i.e. ✔) indicates full support.A missing checkmark indicates key pair authentication is not supported.
Client | Key Pair Authentication | Key Pair Rotation | Unencrypted Private Keys |
|---|---|---|---|
✔ | ✔ | ||
✔ | ✔ | ✔ | |
✔ | ✔ | ✔ | |
✔ | ✔ | ✔ | |
✔ | ✔ | ||
✔ | ✔ | ✔ | |
✔ | ✔ | ✔ | |
✔ | ✔ | ✔ | |
✔ | ✔ | ✔ |
Configuring Key Pair Authentication¶
Complete the following steps to configure key pair authentication for all supported Snowflake clients.
Openssl Generate Rsa Key Pair And Certificate
Step 1: Generate the Private Key¶
Depending on which one of the Supported Snowflake Clients you use to connect to Snowflake, you have the option to generate encrypted orunencrypted private keys. Generally, it is safer to generate encrypted keys. Snowflake recommends communicating with your internal securityand governance officers to determine which key type to generate prior to completing this step.
Tip
The command to generate an encrypted key prompts for a passphrase to regulate access to the key. Snowflake recommends using a passphrasethat complies with PCI DSS standards to protect the locally generated private key. Additionally, Snowflake recommends storing thepassphrase in a secure location. If using an encrypted key to connect to Snowflake, you will input the passphrase during the initialconnection. The passphrase is only used for protecting the private key and will never be sent to Snowflake.
To generate a long and complex passphrase based on PCI DSS standards:
Access the PCI Security Standards Document Library.
For PCI DSS, select the most recent version and your desired language.
Complete the form to access the document.
Search for
Passwords/passphrasesmustmeetthefollowing:and follow the recommendations for password/passphraserequirements, testing, and guidance. Depending on the document version, the phrase is likely located in a section calledRequirement8:Identifyandauthenticateaccesstosystemcomponents(or similar name).
To start, open a terminal window and generate a private key.
You can generate either an encrypted version of the private key or an unencrypted version of the private key.
To generate an unencrypted version, use the following command:
To generate an encrypted version, use the following command (which omits “-nocrypt”):
The commands generate a private key in PEM format.
Step 2: Generate a Public Key¶
From the command line, generate the public key by referencing the private key. The following command assumes the private key is encryptedand contained in the file named rsa_key.p8.
The command generates the public key in PEM format.
Step 3: Store the Private and Public Keys Securely¶
Copy the public and private key files to a local directory for storage. Record the path to the files. Note that the private key is storedusing the PKCS#8 (Public Key Cryptography Standards) format and is encrypted using the passphrase you specified in the previous step.
However, the file should still be protected from unauthorized access using the file permission mechanism provided by your operating system.It is your responsibility to secure the file when it is not being used.
Step 4: Assign the Public Key to a Snowflake User¶
Execute an ALTER USER command to assign the public key to a Snowflake user.
Note
Only security administrators (i.e. users with the SECURITYADMIN role) or higher can alter a user.
Exclude the public key delimiters in the SQL statement.
Step 5: Verify the User’s Public Key Fingerprint¶
Execute a DESCRIBE USER command to verify the user’s public key fingerprint.
Note
The RSA_PUBLIC_KEY_2_FP property is described in Configuring Key Pair Rotation.
Step 6: Configure the Snowflake Client to Use Key Pair Authentication¶
Update the client to use key pair authentication to connect to Snowflake.
Configuring Key Pair Rotation¶
Snowflake supports multiple active keys to allow for uninterrupted rotation. Rotate and replace your public and private keys based on theexpiration schedule you follow internally.
Currently, you can use the RSA_PUBLIC_KEY and RSA_PUBLIC_KEY_2 parameters for ALTER USER toassociate up to 2 public keys with a single user.
Complete the following steps to configure key pair rotation and rotate your keys.
Complete all steps in Configuring Key Pair Authentication with the following updates:
Generate a new private and public key set.
Assign the public key to the user. Set the public key value to either
RSA_PUBLIC_KEYorRSA_PUBLIC_KEY_2(whicheverkey value is not currently in use). For example:
Update the code to connect to Snowflake. Specify the new private key.
Snowflake verifies the correct active public key for authentication based on the private key submitted with your connection information.
Remove the old public key from the user profile using an ALTER USER command.
Not too long ago, I wanted to know how to generate the public-keys that OpenSSH generates, as a transitional step to understanding how to decode them. In this fashion, I might apply the knowledge, some day, to a dynamically configurable SSH platform to allow a client to connect via SSH and to authenticate against a database, such as with Github and Bitbucket.
Openssl Generate Rsa Key Pair C++
What I did not learn while painfully trolling and reverse-engineering all of the key-generation code for ssh-keygen was that this representation is described by PKCS8. Yes, more than a little time was unnecessarily wasted. In fact, you can generate PKCS8-formatted public keys with OpenSSL.
Needless to say, I never finished reverse-engineering the code. This wasn’t so much because it became a monster, but rather the code was unfathomably ugly. It would’ve taken an enormous amount of time to hack something together, and the same amount of time to refactor it into being something elegant. It required too much of a commitment for something without an immediate need. It would’ve been quicker (and funnier) to write a FUSE wrapper to read the database, and just point OpenSSH to the mountpoint.
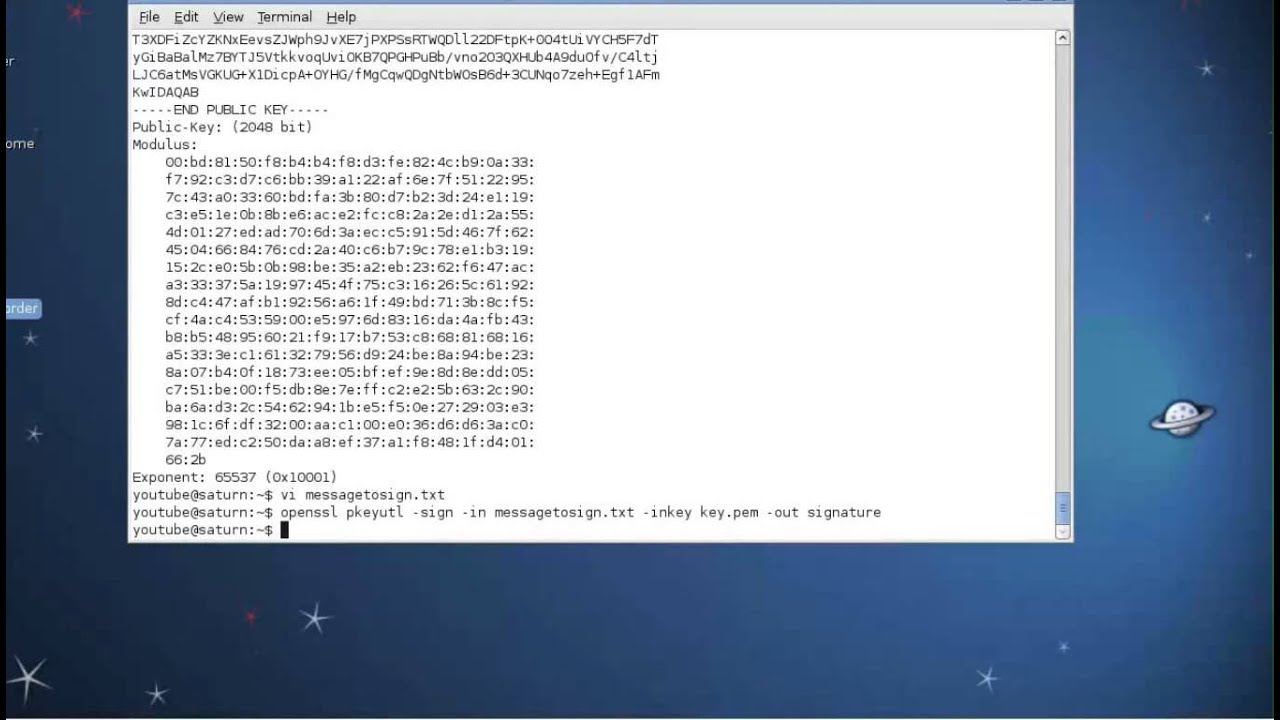
Generating an RSA public-key and converting it to PKCS8:
The parameters to ssh-keygen simply indicate that the data is coming from STDIN, we’re doing an import, and the key-format is PKCS8.
Also, with DSA:
I included DSA because generating a key-pair with DSA for general PKE is a bit more obscure. I don’t know why. It is still possible, however.
Openssl Rsa Generate Key Pair Chart
Lastly, ECDSA (elliptic-curve DSA), for completeness. This is really the one that you want to be using, if given a choice. See how cute/short the public-keys are for an algorithm with considerably-more strength? A 256-bit curve is equivalent to a traditional 3072-bit RSA key.